Information Security
FIDO Authentication
FIDO Authentication is the answer to the global password problem.
With FIDO Authentication, users sign in with phishing resistant credentials, called passkeys. Passkeys can be synced across devices or bound to a platform or security key and enable password-only logins to be replaced with secure and fast login experiences across websites and apps.
Passkeys are more secure than passwords and SMS OTPs, simpler for consumers to use,and easier for service providers to deploy and manage

FIDO allows users to simply sign in with passkeys across their devices with a biometric or a security key

FIDO Authentication can be implemented across a wide variety of use cases across markets

Regulated Industries

Enterprise
Consumer
SIEM solution
Security information and event management (SIEM).
Security information and event management (SIEM) is a subfield of computer security that combines security information management (SIM) and security event management (SEM) (SEM). They analyse security alerts generated by applications and network hardware in real time. SIEM is sold by vendors as software, appliances, or managed services; these products are also used to log security data and generate compliance reports.

SIEM Capabilities
Cloud Security
Configuration Assessment
Containers Security
File Integrity Monitoring
Incident Response
Intrusion Detection
Log Data Analysis
Regulatory Compliance
Security Analytics
Vulnerability Detection
An open source cybersecurity platform that integrates SIEM and XDR in a unique solution.

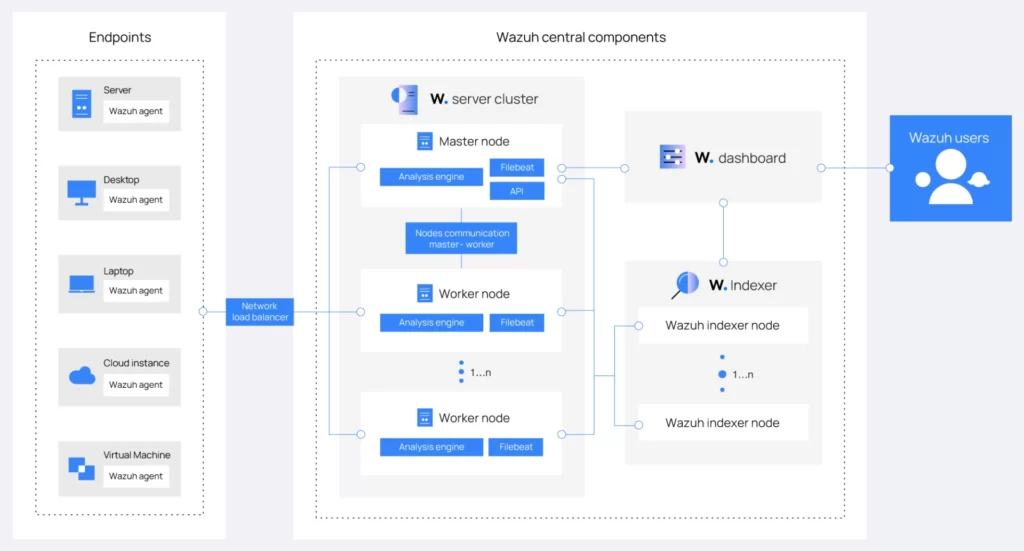
Central Components

SIEM indexer
The SIEM indexer is a full-text search and analysis engine that is highly scalable. It is responsible for indexing and storing alerts generated by the SIEM server. Depending on the environment, it can be installed as a single-node or multi-node cluster.

SIEM dashboard
A versatile and user-friendly web interface for data mining, analysis, and visualization. The dashboard is used to manage and monitor the SIEM configuration.

SIEM server
The server manages the agents, remotely configuring and updating them as needed. This component examines data received from agents, processing it through decoders and rules and employing threat intelligence to look for indicators of compromise.
Endpoint Security Agent
SIEM agent
The SIEM agent is a multi-platform component that runs on the endpoints to be monitored.
It provides prevention, detection, and response capabilities.
What We Offer
FIDO Authentication
FIDO Authentication is the answer to the global password problem.
With FIDO Authentication, users sign in with phishing resistant credentials, called passkeys. Passkeys can be synced across devices or bound to a platform or security key and enable password-only logins to be replaced with secure and fast login experiences across websites and apps.
Passkeys are more secure than passwords and SMS OTPs, simpler for consumers to use,and easier for service providers to deploy and manage

FIDO allows users to simply sign in with passkeys across their devices with a biometric or a security key

FIDO Authentication can be implemented across a wide variety of use cases across markets

Regulated Industries

Regulated Industries

Regulated Industries
SIEM solution
Security information and event management (SIEM).
Security information and event management (SIEM) is a subfield of computer security that combines security information management (SIM) and security event management (SEM) (SEM). They analyse security alerts generated by applications and network hardware in real time. SIEM is sold by vendors as software, appliances, or managed services; these products are also used to log security data and generate compliance reports.

SIEM Capabilities
Cloud Security
Configuration Assessment
Containers Security
File Integrity Monitoring
Incident Response
Intrusion Detection
Log Data Analysis
Regulatory Compliance
Security Analytics
Vulnerability Detection
An open source cybersecurity platform that integrates SIEM and XDR in a unique solution.
Central Components
SIEM indexer
The SIEM indexer is a full-text search and analysis engine that is highly scalable. It is responsible for indexing and storing alerts generated by the SIEM server. Depending on the environment, it can be installed as a single-node or multi-node cluster.
SIEM dashboard
A versatile and user-friendly web interface for data mining, analysis, and visualization. The dashboard is used to manage and monitor the SIEM configuration.
SIEM server
The server manages the agents, remotely configuring and updating them as needed. This component examines data received from agents, processing it through decoders and rules and employing threat intelligence to look for indicators of compromise.
Endpoint Security Agent
SIEM agent
The SIEM agent is a multi-platform component that runs on the endpoints to be monitored.
It provides prevention, detection, and response capabilities.